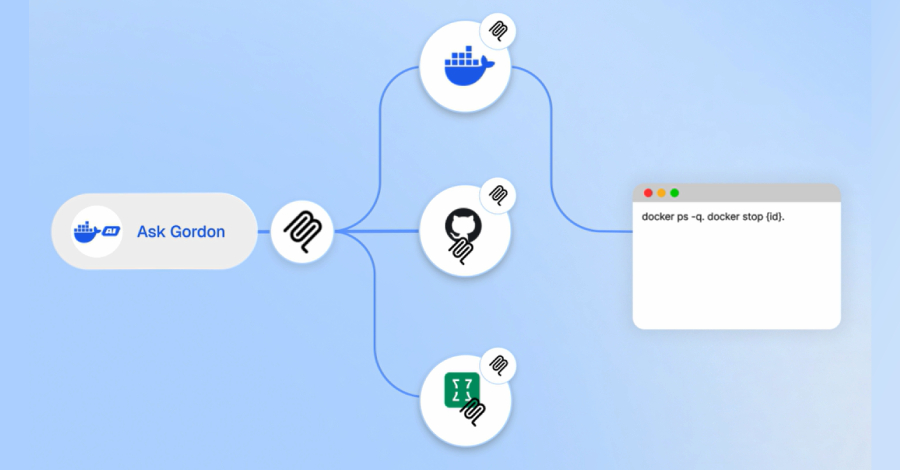
Ravie LakshmananFeb 03, 2026Artificial Intelligence / Vulnerability Cybersecurity researchers have disclosed details of a now-patched security flaw impacting Ask Gordon,
Ravie LakshmananFeb 03, 2026Open Source / Vulnerability Threat actors have been observed exploiting a critical security flaw impacting the Metro
The Hacker NewsFeb 03, 2026Threat Detection / Enterprise Security Most security teams today are buried under tools. Too many dashboards.
Recent major cloud service outages have been hard to miss. High-profile incidents affecting providers such as AWS, Azure, and Cloudflare
Ravie LakshmananFeb 03, 2026Vulnerability / Malware The Russia-linked state-sponsored threat actor known as APT28 (aka UAC-0001) has been attributed to
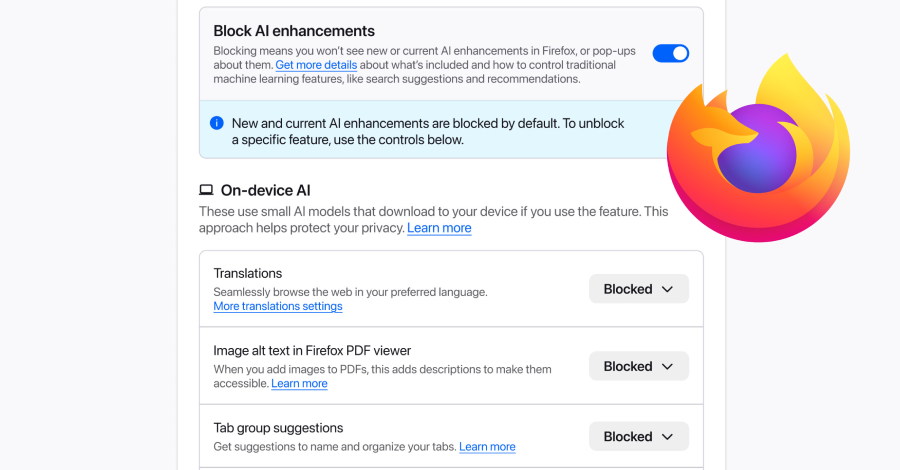
Ravie LakshmananFeb 03, 2026Artificial Intelligence / Privacy Mozilla on Monday announced a new controls section in its Firefox desktop browser
Ravie LakshmananFeb 03, 2026Malware / Open Source A China-linked threat actor known as Lotus Blossom has been attributed with medium
A security audit of 2,857 skills on ClawHub has found 341 malicious skills across multiple campaigns, according to new findings
Ravie LakshmananFeb 02, 2026Vulnerability / Artificial Intelligence A high-severity security flaw has been disclosed in OpenClaw (formerly referred to as
A prolific data ransom gang that calls itself Scattered Lapsus Shiny Hunters (SLSH) has a distinctive playbook when it seeks