Picture this: you stumble upon a concealed secret within your company’s source code. Instantly, a wave of panic hits as
Jan 04, 2024The Hacker NewsEthical Hacking / Vulnerability Assessment Section four of the “Executive Order on Improving the Nation’s Cybersecurity”
Jan 04, 2024NewsroomSoftware Security / Malware The threat actor known as UAC-0050 is leveraging phishing attacks to distribute Remcos RAT
Jan 03, 2024NewsroomMalware / Data Theft Information stealing malware are actively taking advantage of an undocumented Google OAuth endpoint named
Jan 02, 2024NewsroomData Privacy / Online Tracking Google has agreed to settle a lawsuit filed in June 2020 that alleged
Jan 02, 2024The Hacker NewsBrowser Security / Threat Protection Security stakeholders have come to realize that the prominent role the
Jan 01, 2024NewsroomEncryption / Network Security Security researchers from Ruhr University Bochum have discovered a vulnerability in the Secure Shell
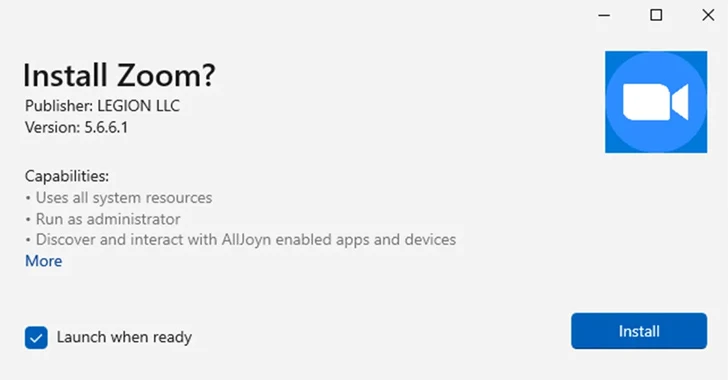
Jan 01, 2024NewsroomWindows Security / Vulnerability Security researchers have detailed a new variant of a dynamic link library (DLL) search
Dec 29, 2023NewsroomMalware / Endpoint Security Microsoft on Thursday said it’s once again disabling the ms-appinstaller protocol handler by default
Dec 29, 2023NewsroomEmail Security / Malware The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of a new phishing