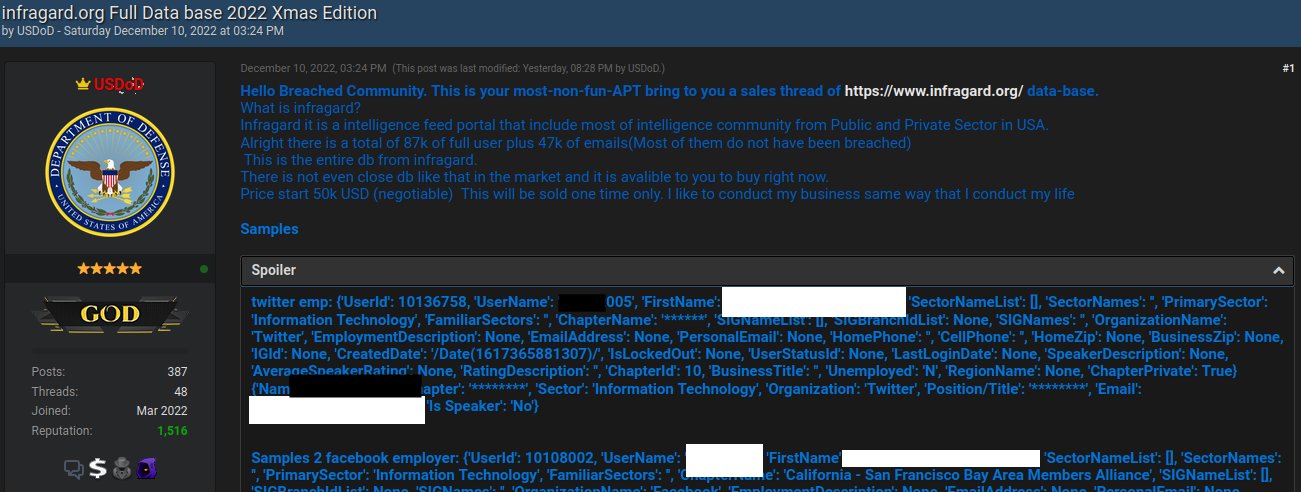
Brazilian authorities reportedly have arrested a 33-year-old man on suspicion of being “USDoD,” a prolific cybercriminal who rose to infamy
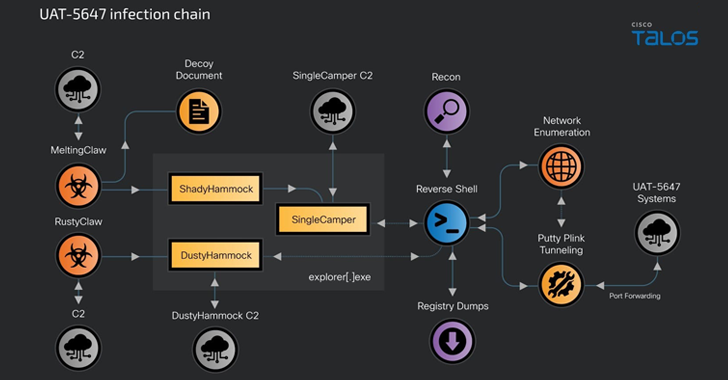
Oct 17, 2024Ravie LakshmananThreat Intelligence / Malware The Russian threat actor known as RomCom has been linked to a new
The parents of a 19-year-old Connecticut honors student accused of taking part in a $243 million cryptocurrency heist in August
Oct 04, 2024Ravie LakshmananPhishing Attack / Cybercrime Microsoft and the U.S. Department of Justice (DoJ) on Thursday announced the seizure
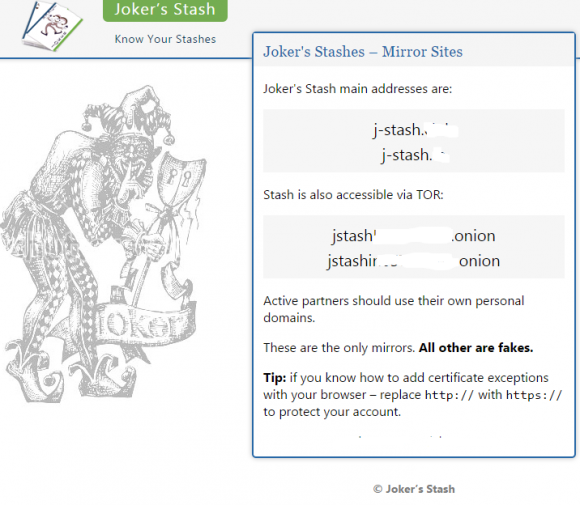
The United States today unveiled sanctions and indictments against the alleged proprietor of Joker’s Stash, a now-defunct cybercrime store that
In IT environments, some secrets are managed well and some fly under the radar. Here’s a quick checklist of what
Law enforcement authorities have announced the takedown of an international criminal network that leveraged a phishing platform to unlock stolen
Sep 21, 2024Ravie LakshmananNational Security / Cyber Attack Ukraine has restricted the use of the Telegram messaging app by government
Sep 21, 2024Ravie LakshmananPrivacy / Artificial Intelligence The U.K. Information Commissioner’s Office (ICO) has confirmed that professional social networking platform
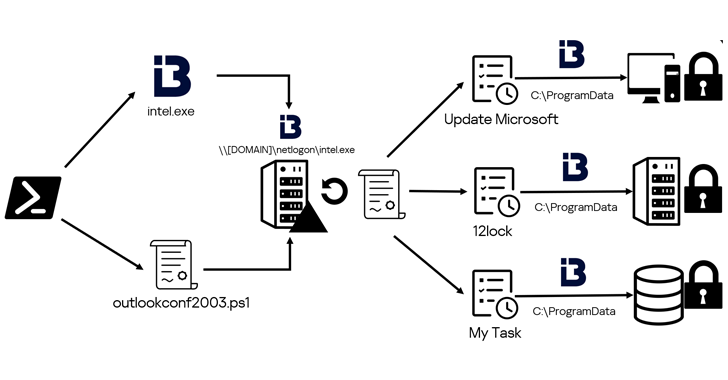
A hacktivist group known as Twelve has been observed using an arsenal of publicly available tools to conduct destructive cyber