Federal prosecutors in Los Angeles this week unsealed criminal charges against five men alleged to be members of a hacking
Nov 22, 2024Ravie LakshmananArtificial Intelligence / Malware Cybersecurity researchers have discovered two malicious packages uploaded to the Python Package Index
In December 2023, KrebsOnSecurity revealed the real-life identity of Rescator, the nickname used by a Russian cybercriminal who sold more
Nov 09, 2024Ravie LakshmananVulnerability / Network Security Palo Alto Networks on Friday issued an informational advisory urging customers to ensure
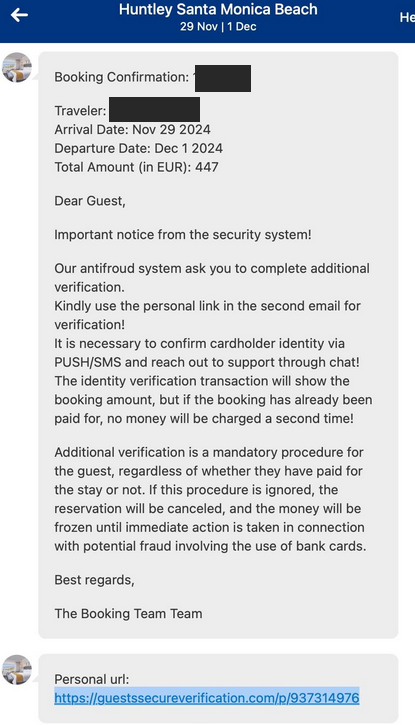
A number of cybercriminal innovations are making it easier for scammers to cash in on your upcoming travel plans. This
Oct 26, 2024Ravie LakshmananCloud Security / Cryptocurrency The infamous cryptojacking group known as TeamTNT appears to be readying for a
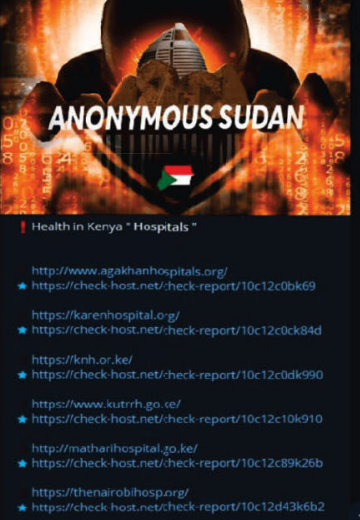
The U.S. government on Wednesday announced the arrest and charging of two Sudanese brothers accused of running Anonymous Sudan (a.k.a.
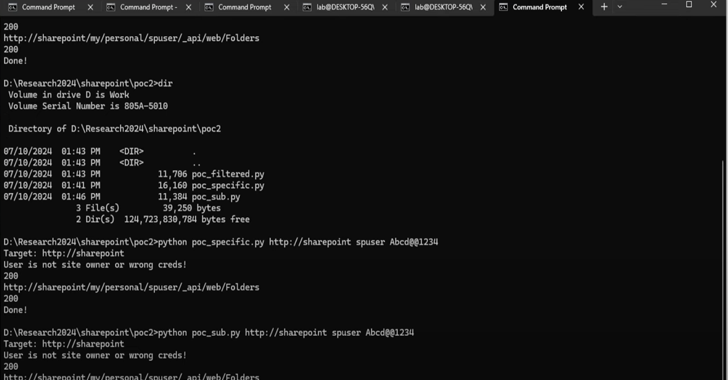
Oct 23, 2024Ravie LakshmananVulnerability / Threat Intelligence A high-severity flaw impacting Microsoft SharePoint has been added to the Known Exploited
Not long ago, the ability to digitally track someone’s daily movements just by knowing their home address, employer, or place
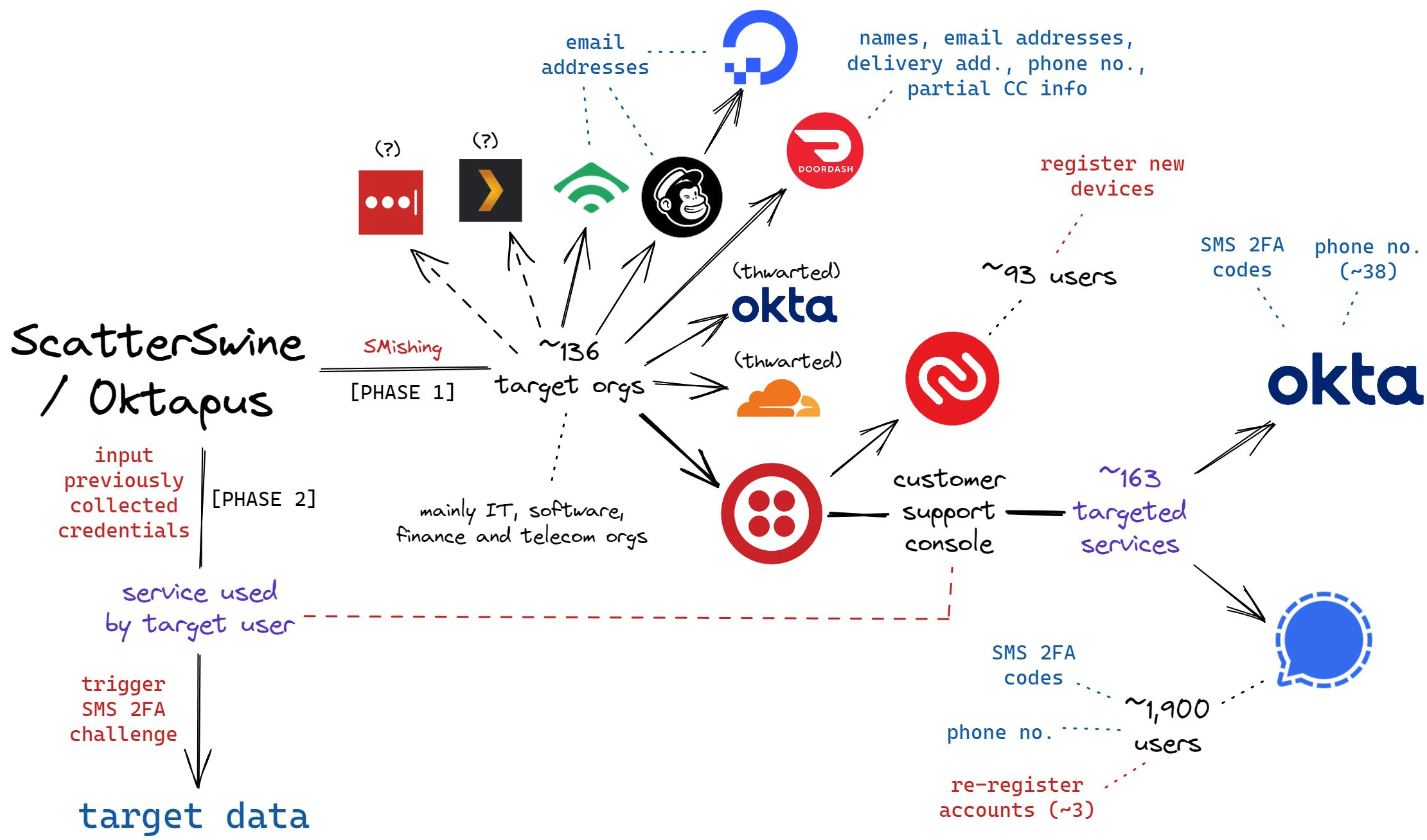
Oct 23, 2024The Hacker NewsIdentity Security / Data Protection Identity security is front, and center given all the recent breaches