Cybercriminals are selling hundreds of thousands of credential sets stolen with the help of a cracked version of Acunetix, a
Dec 24, 2024Ravie LakshmananVulnerability / Zero Day The Apache Software Foundation (ASF) has released a security update to address an
A financial firm registered in Canada has emerged as the payment processor for dozens of Russian cryptocurrency exchanges and websites
Microsoft closed out its Patch Tuesday updates for 2024 with fixes for a total of 72 security flaws spanning its
Phishing attacks increased nearly 40 percent in the year ending August 2024, with much of that growth concentrated at a
Nov 27, 2024Ravie LakshmananVulnerability / Software Security A critical security flaw impacting the ProjectSend open-source file-sharing application has likely come
Microsoft today released updates to plug at least 89 security holes in its Windows operating systems and other software. November’s
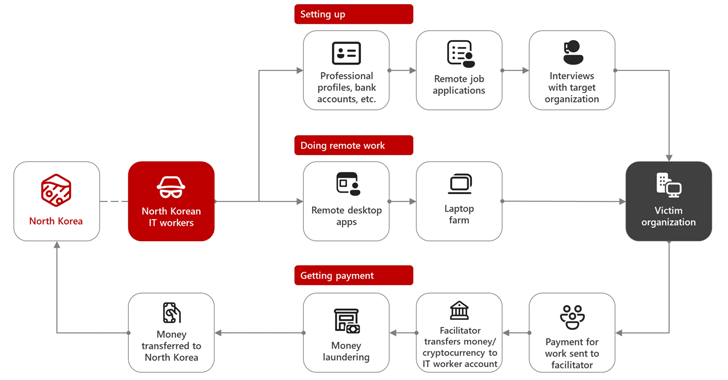
Nov 23, 2024Ravie LakshmananArtificial Intelligence / Cryptocurrency The North Korea-linked threat actor known as Sapphire Sleet is estimated to have
The financial technology firm Finastra is investigating the alleged large-scale theft of information from its internal file transfer platform, KrebsOnSecurity
Nov 23, 2024Ravie LakshmananCloud Security / Threat Intelligence Government agencies and non-governmental organizations in the United States have become the