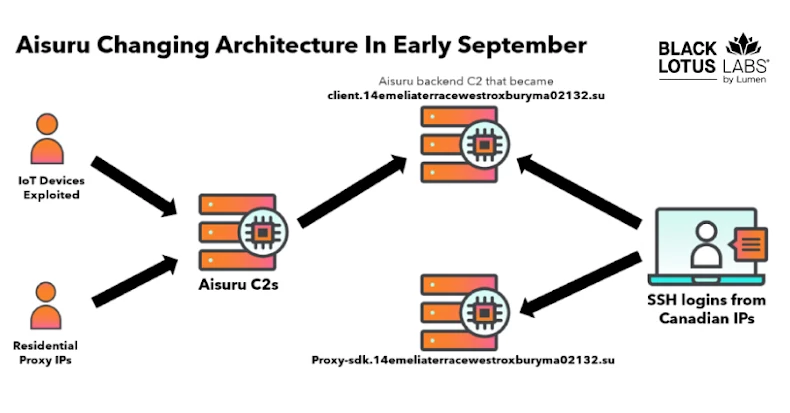
The Black Lotus Labs team at Lumen Technologies said it null-routed traffic to more than 550 command-and-control (C2) nodes associated
AI agents have quickly moved from experimental tools to core components of daily workflows across security, engineering, IT, and operations.
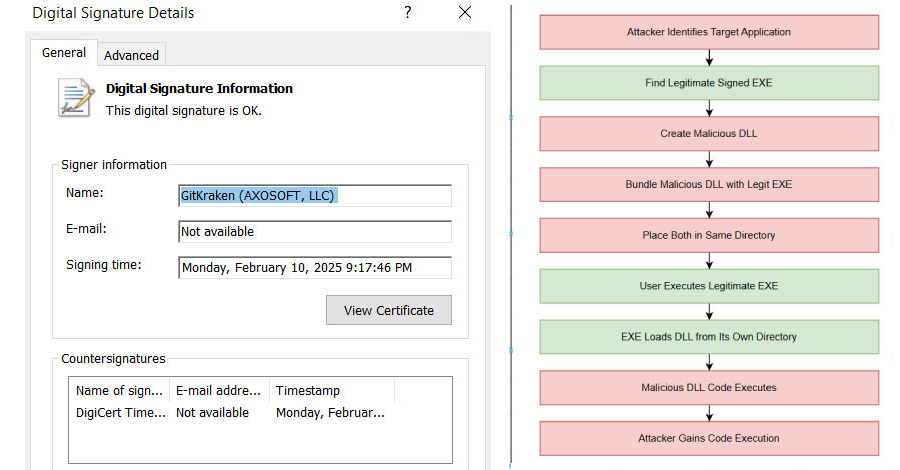
Security experts have disclosed details of an active malware campaign that’s exploiting a DLL side-loading vulnerability in a legitimate binary
Jan 14, 2026Ravie LakshmananVulnerability / Patch Management Fortinet has released updates to fix a critical security flaw impacting FortiSIEM that
Microsoft on Tuesday rolled out its first security update for 2026, addressing 114 security flaws, including one vulnerability that it
Research analyzing 4,700 leading websites reveals that 64% of third-party applications now access sensitive data without business justification, up from
Jan 14, 2026Ravie LakshmananApplication Security / Vulnerability Node.js has released updates to fix what it described as a critical security
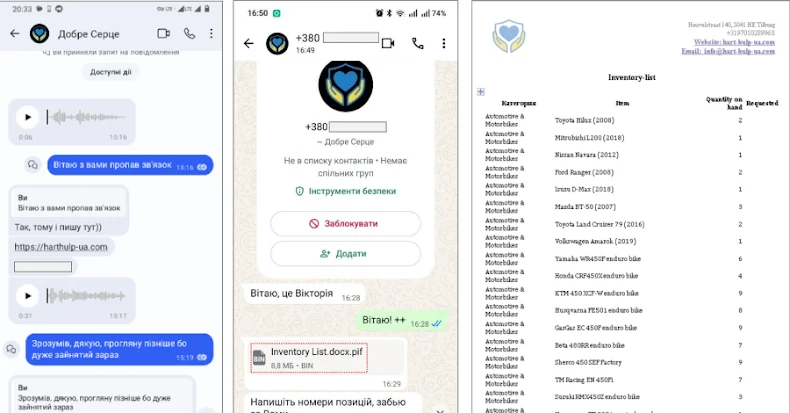
Jan 14, 2026Ravie LakshmananCyber Espionage / Threat Intelligence The Computer Emergency Response Team of Ukraine (CERT-UA) has disclosed details of
Microsoft today issued patches to plug at least 113 security holes in its various Windows operating systems and supported software.
Jan 13, 2026Ravie Lakshmanan Web Security / Data Theft Cybersecurity researchers have discovered a major web skimming campaign that has